NOTE TO READERS: The Catch of the Day blog not only posts examples of phishing, fraud, and other malicious emails, but also best practices and general CIS news items. This is one of them! You can always locate best practices and news items by clicking on any category (right-hand sidebar).
On November 28th, a serious vulnerability was discovered in the Apple Mac operating system High Sierra. This vulnerability allows a bad actor to gain complete control of a user’s computer, which could lead to the loss of important data and the installation of malicious software (malware).
Apple released a fix and we advise everyone who uses High Sierra to apply the critical security update to their Apple machine. Computing and Information Services currently does not deploy or support High Sierra on Vassar-owned machines. However, we want to ensure that student machines and personally-owned machines are updated, as any compromised machine on campus could affect the Vassar community.
If you have a Vassar-owned machine that is running Sierra, El Capitan, or an earlier operating system, please do not upgrade it to High Sierra as it may disrupt the functionality of your machine.
(Click “Continue Reading” for instructions)
- Click on the Apple icon (upper left corner of your computer)
- Click “About This Mac” from the menu
- If your computer says “MacOS High Sierra” as shown below, you need to apply the patch. If your computer shows any other operating system, no additional action is necessary

- Click on the Apple icon (upper left corner of your computer)
- Click “App Store” from the menu
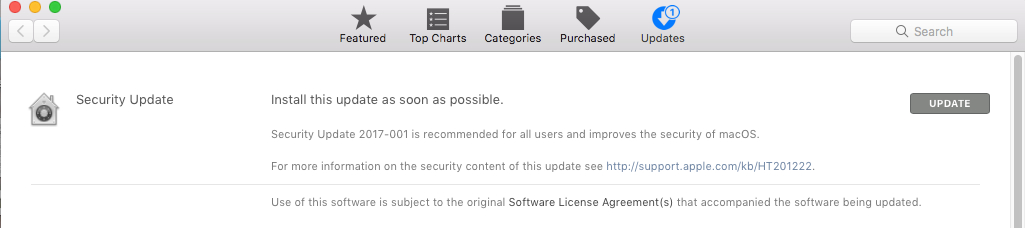
- Click “Updates”
- The security update should be the very first update listed. Click “Update” to initiate the process
- This update does not require you to reboot your machine